A few characteristics of the Ransomware
The latest spin on a ransom is not related to the letters clipped out of a magazine or newspaper. In the recent years, criminals are relying on advanced methods to attacks your PCs and data through a malicious software known as ransomware.
Is not it exasperating when your PC is sluggish due to the presence of a virus? However, what is virus encrypts your data so you cannot have access to it or install some pornography on your screen? It is often that Ransomware attacks often rely on these tactics. There are some key characteristics which set Ransomware apart from several other malware. Some of these characteristics are mentioned below:
- It features unbreakable encryption. In other words, it means that you cannot decrypt the files on your own. There are several decryption tools which are released by the cyber security researchers.
- This particular type of malware can encrypt all types of files. From videos to pictures, documents, audio files and other things that you have on your PC, it can encrypt anything and everything.
- It can easily scramble your file names. Thus, you cannot find out which data was affected. This is a social engineering trick which is often used for coercing and confusing victims into paying the ransom.
![]()
- It will end up adding a different extension to your files for showing a signal of a particular type of ransomware strain
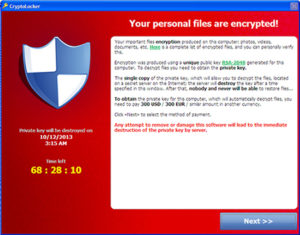
- It will display a message or an image that lets a person know that the data has been encrypted and you have to now shell out some specific amount of money to get it back.
- It requires you to make payment in Bitcoins as this crypto currency cannot be tracked by the experts and researchers of the cyber security or other law enforcement agencies.
- In most cases, there is a time limit for ransom payments for adding another level of psychological constraint to this type of extension scheme. If you do not pay the ransom on time then the ransom will increase, however, it can also mean that the data will be destroyed forever or destroyed.
- It makes use of a complex set of evasion method so that it cannot be detected by traditional antivirus.
- In most cases, it recruits the infected PCs into botnets, thus cyber criminals expand the infrastructure and further fuel their future attacks.
- It can easily spread to other PCs that are connected to a local network. This, in turn, would create further damage.
- It features data exfiltration capabilities. In other words, it can extract the data easily from the affected computers (for example, email addresses, passwords and usernames to name a few) and send the same to the server controlled and managed by cyber criminals. Remember that the encrypting files are not always the endgame.
- It can also include geographical targeting as well. it means the ransom not is translated into the language of the victim for increasing the possibilities of the ransom to be paid.
These are some of the characteristics of the latest ransomware attack.


Comments are closed.